
You are a forensic analyst investigating a critical ransomware attack at a major financial institution. Your job is to analyze the memory image from the affected endpoint. Trace the attack from its origin, identify lateral movements, uncover persistence methods, and analyze any control commands.
You are a forensic analyst responding to a ransomware incident at a prominent financial institution. A workstation was compromised, and an in-memory artifact was captured for analysis. Your mission is to dissect this memory image to trace the ransomware's point of entry, determine how it executed, and understand its progression through the system.
Category: Endpoint Forensics
Tools: Volatility 3 MemProcFS Event Log Explorer EvtxECmd Timeline Explorer
Q1: Understanding the entry point of the malware is crucial for analyzing the attack vector. Can you specify the filename of the .iso file that was used to deliver the malicious payload?

After deployed the machine, We have filescan output and the memory dump as the evidence on this lab so we gonna need MemprocFS and Volatility 3 to handle this memory dump.
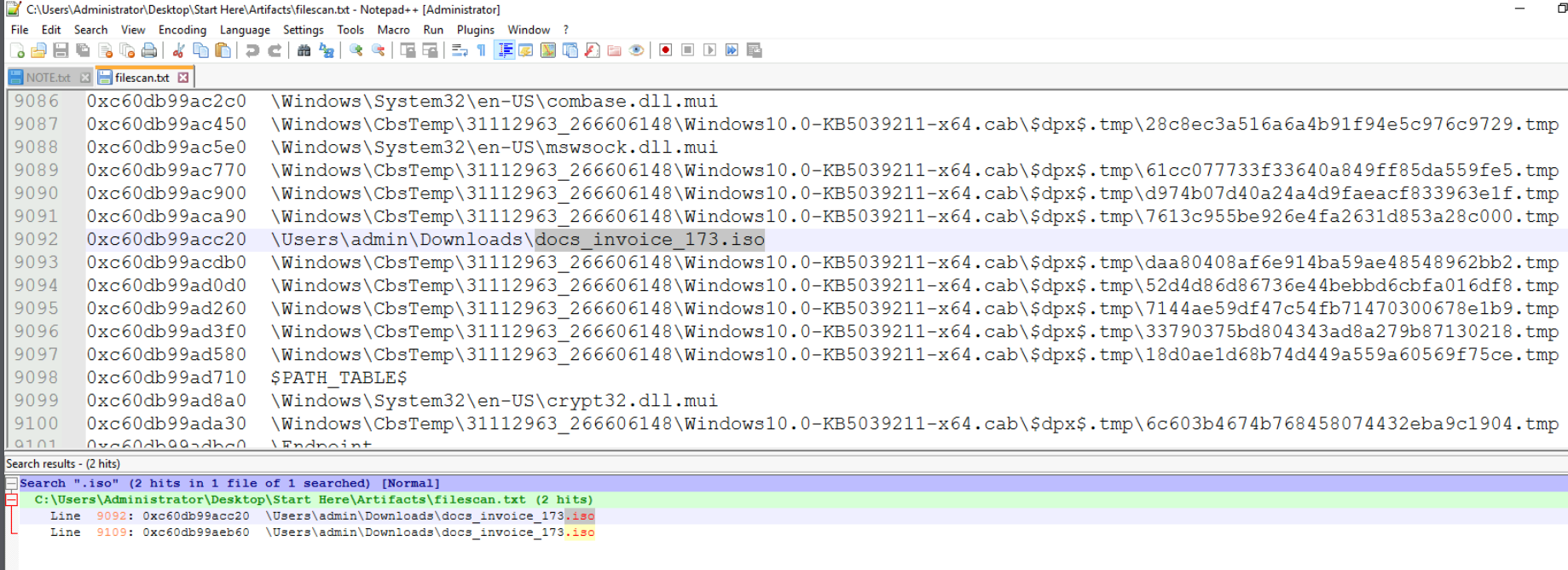
Since the question was asking for ISO file then we could just search on this file from the file scan result which we can see that there is docs_invoice_173.iso file located on the Downloads folder of admin user.
To confirm this, I used MemProcFS to auto-extract some of the files I needed and sometimes the timeline generated by the forensic mode of this tool is very useful. the tool will mount to the M drive by default and it will take a while (10 minutes 43 seconds in my case) to complete forensic mode.
Command : memprocfs.exe -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\memory.dmp" -forensic 1
We know that the ISO file has to be mounted then we can use Event Log Explorer to read Windows VHDMP Operational log right here.
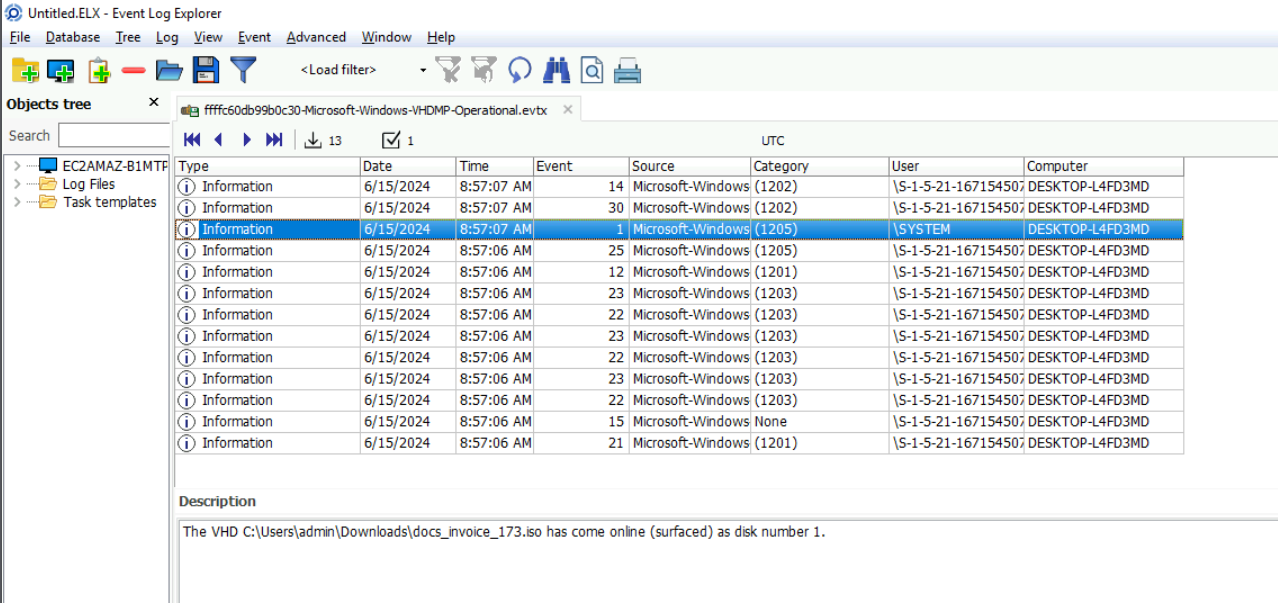
We can see that this iso file was indeed mounted.
docs_invoice_173.iso
Q2: The initial delivery of the malware is crucial for understanding the attack vector. What is the link used to view the malicious malware?
Lets take a look at the Chrome browser history of the "admin" user as the sole user we have on this memory dump.
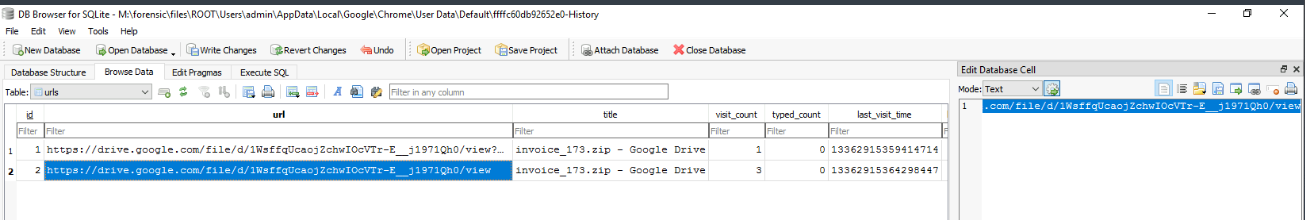
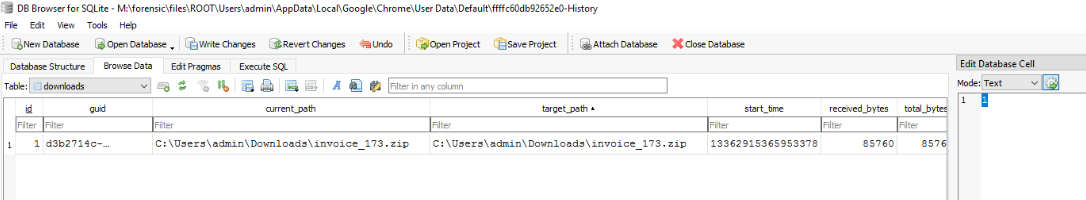
We can see that the user was downloaded the iso file from Google Drive.
https://drive.google.com/file/d/1WsffqUcaojZchwIOcVTr-E__j1971Qh0/view
Q3: Identifying the storage location of a rogue process is critical for assessing its origin and purpose within a compromised system. What is the directory path where this process is located on the workstation?
C:\Users\admin\Downloads
Q4: To track the timeline of the attack, it is essential to know when the malware was dropped on the system. What is the download date and time of the malicious file on the affected device?
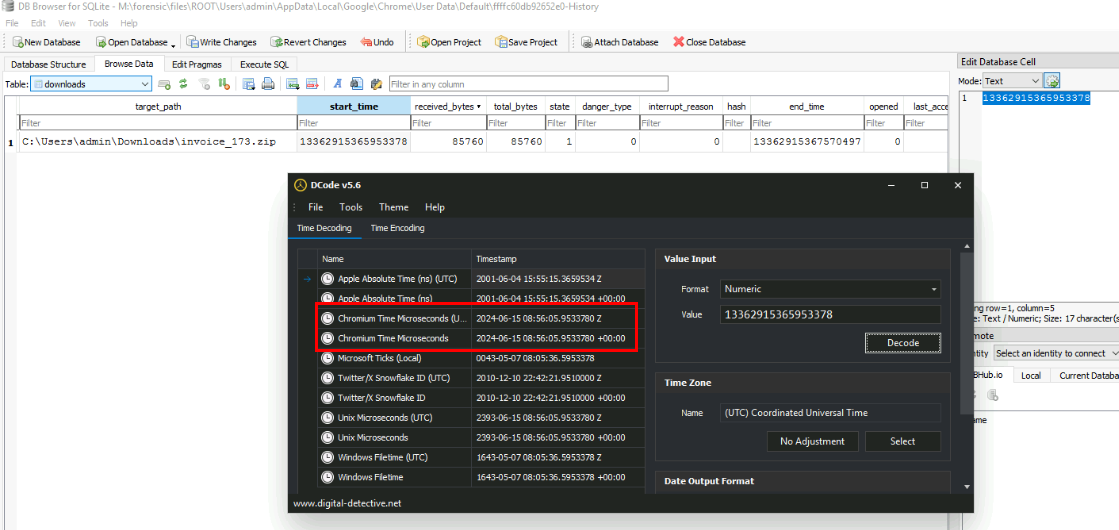
We can use D-code to convert Chrome timestamp to UTC and get the answer to this question.
2024-06-15 08:56
Q5: Determining the root of the malicious activity is essential for comprehending the extent of the intrusion. What is the malicious command that triggered this malicious behavior?
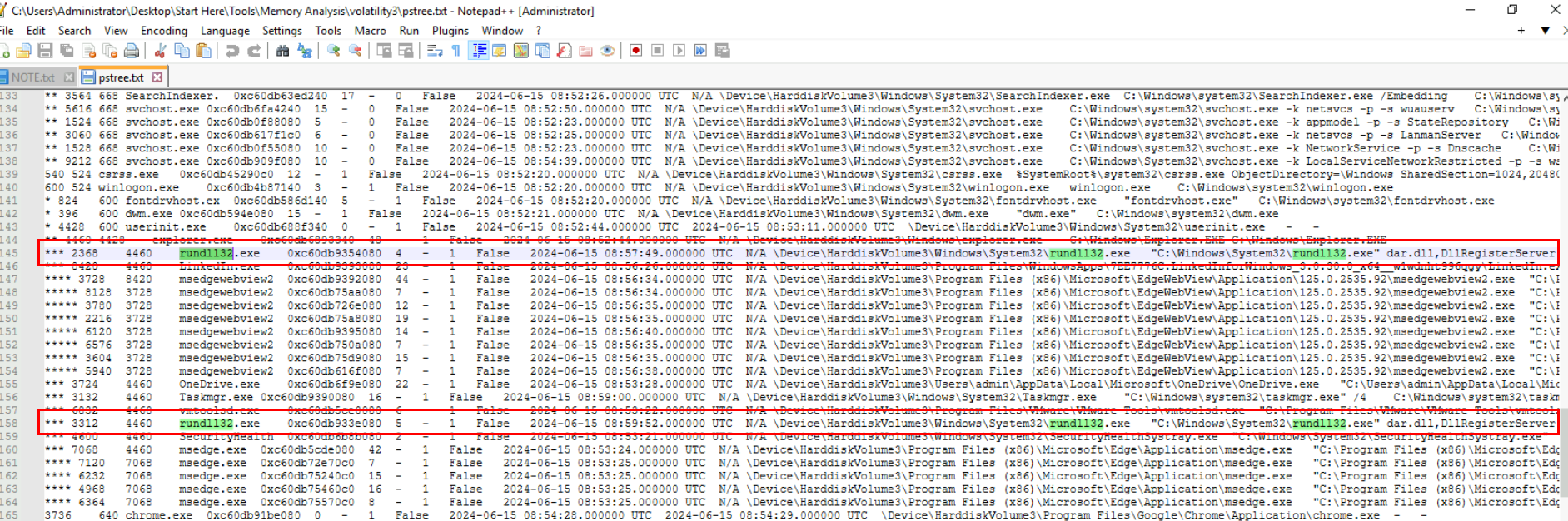
I ran pstree to find any suspicious process that should not be there which I found that there is 2 rundll32.exe (PID 2368 and 3312) process that was executed dar.dll process which is weird since we usually see the full path of the dll that was loaded by rundll32.exe in full path but it could mean this dll was located on the mounted disk of ISO file.
Command : python vol.py -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\memory.dmp" windows.pstree > pstree.txt
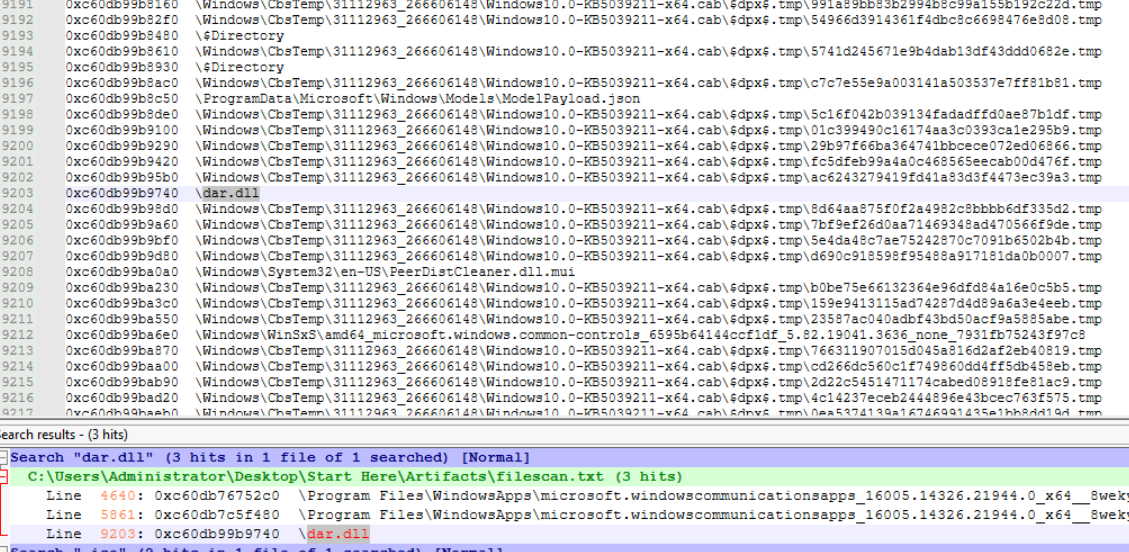
After searching this file from the windows.filescan result, we can see that it might really be in the mounted drive.
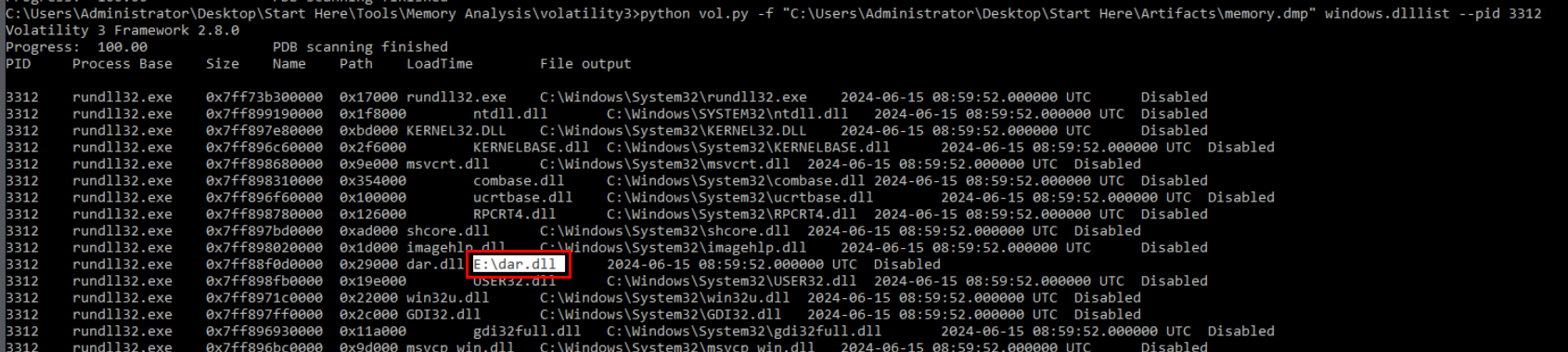
Then I listed the dll/modules that was loaded into process with PID 3312 and We can see that this file was indeed triggered from the C drive and if we did some research on this malware and this specific file then we can confirm that this is the IcedID malware as the lab name explicitly stated.
Command : python vol.py -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\memory.dmp" windows.dllist --pid 3312
rundll32.exe dar.dll,DllRegisterServer
Q6: Identifying file indicators is crucial for a comprehensive forensic analysis. What is the SHA256 hash of the DLL associated with the last execution of the malware?
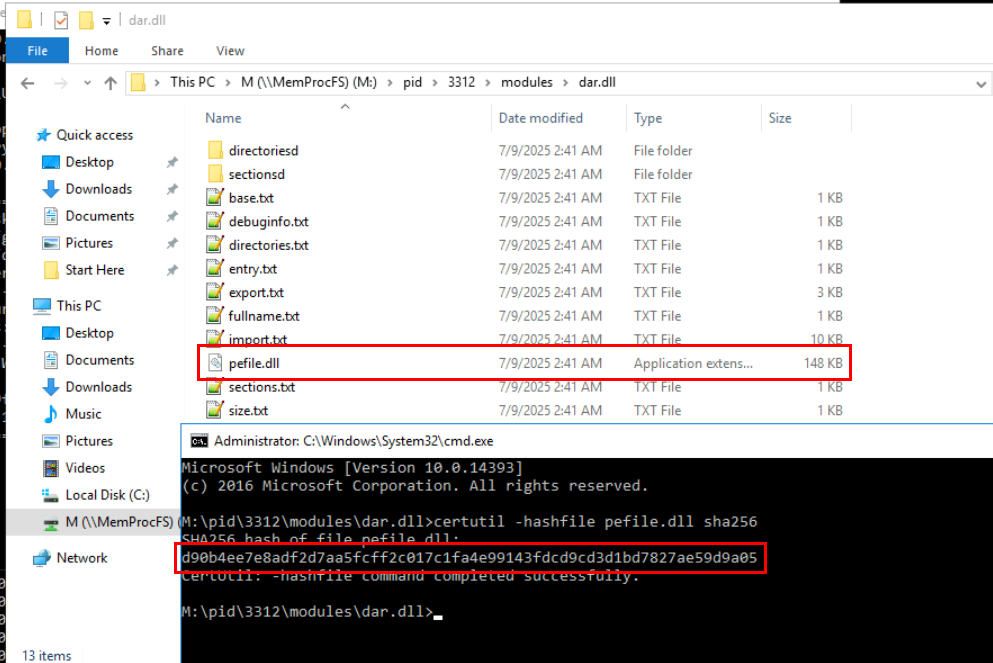
Now we can take a look at this dll by going to the dar.dll modules folder and calculate filehash of this file.
Command : certutil -hashfile pefile.dll sha256
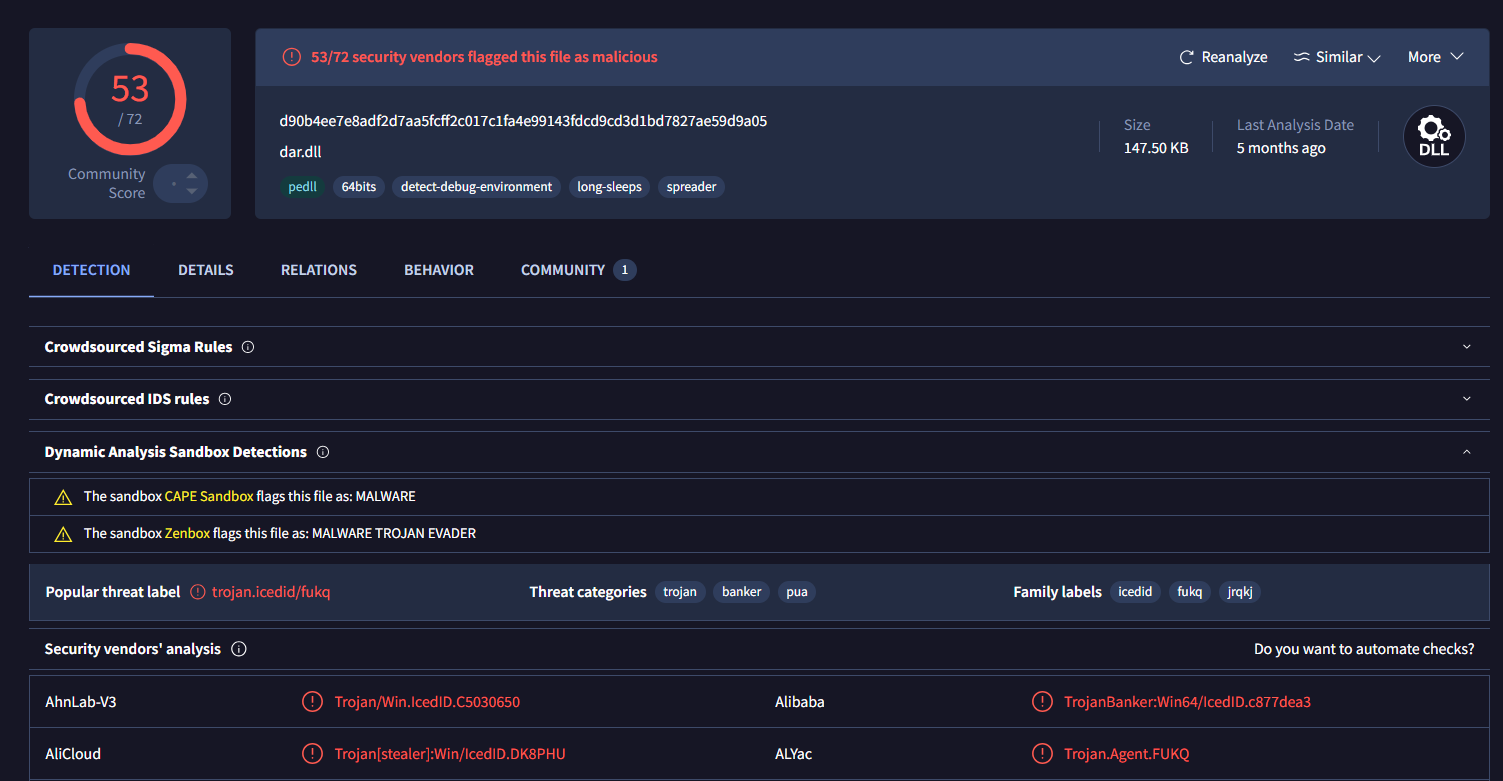
VirusTotal confirmed that this file is indeed IcedID
d90b4ee7e8adf2d7aa5fcff2c017c1fa4e99143fdcd9cd3d1bd7827ae59d9a05
https://cyberdefenders.org/blueteam-ctf-challenges/achievements/Chicken_0248/icedid-2/
Once I finished the lab, I searched for the dar.dll file online and found that there are so many blog/report that have covered the same ISO file and the notable resources are
- Quantum Ransomware by The DFIR Report
- Cybereason vs. Quantum Locker Ransomware
- IcedID-IcedID Beacon -Hunting, Preventing, and Responding to IcedID Malware using Logpoint
So I recommended my readers to read one of these contents to learn more about this malware